Continuation of ILDVR INC-MH40D06
Since manufacturer will not divulge the super secret telnet password, and not having ability to turn off the telnet from web ui, I have decided to get access to camera via more brute method.
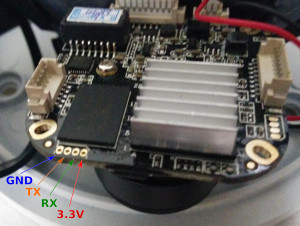
This involves opening the camera, soldering a pin header/wires to RS232 pads on the SoC board:
The RS232 is connected to a 3.3V (NOT 5V!) USB RS232 TTL adapter (a few bucks on ebay). BTW the ebay sourced USB adapter did not come with instruction/pin-out. It is in fact the following:
Red - 3.3V
Green - TX
White - RX
Black - GND
The pin spacing is 1.27mm. I could not find the connector that would fit so I botched 1.27mm->2.54mm header adapter (since the USB adapter came with 2.54mm sockets):
I disconnected the 3.3V pin as the SoC was using that for power and would not reboot when PoE was disconnected.
I used minicom with following settings:
115200 8N1
ttyUSB0
Once power is applied immediately press any key to interrupt the boot process and get uBoot prompt:
U-Boot 2010.06 (May 18 2015 - 09:40:27)
Check spi flash controller v350... Found
Spi(cs1) ID: 0xC2 0x20 0x18 0xC2 0x20 0x18
Spi(cs1): Block:64KB Chip:16MB Name:"MX25L128XX"
In: serial
Out: serial
Err: serial
Hit any key to stop autoboot: 0
hisilicon #To find out correct boot parameters run printenv:
hisilicon # printenv
bootcmd=sf probe 0;sf read 0x82000000 0x50000 0x2b0000;bootm 0x82000000
bootdelay=1
baudrate=115200
ethaddr=00:00:23:34:45:66
ipaddr=192.168.6.99
serverip=192.168.6.10
netmask=255.255.252.0
bootfile="uImage"
board=hi3516d
bootargs=mem=128M console=ttyAMA0,115200 root=/dev/mtdblock2 rootfstype=jffs2 mtdparts=hi_sfc:320K(boot),2752K(kernel),2M(rootfs),11M(data)
stdin=serial
stdout=serial
stderr=serial
verify=n
ver=U-Boot 2010.06 (May 18 2015 - 09:40:27)To get root you will need to modify the bootargs variable:
setenv bootargs mem=128M console=ttyAMA0,115200 root=/dev/mtdblock2 rootfstype=jffs2 mtdparts=hi_sfc:320K(boot),2752K(kernel),2M(rootfs),11M(data) init=/bin/shIt is pretty much exactly the same as original bootargs from printenv except the init is changed to shell (/bin/sh).
To boot, simply run the values from bootcmd variable from printenv:
sf probe 0;sf read 0x82000000 0x50000 0x2b0000;bootm 0x82000000To continue with boot (to get rest of the mounts and things up and running) run following:
/etc/init.d/rcSAt this stage you can change the root password (via passwd). This will not stick, to make it stick modify Server.tar.xz with desired etc/passwd entry (see below).
Horrible stuff below.
Everything runs as root!
The point of interest is /mnt/flash/Server.tar.xz, I believe init script unpacks it into /mnt/flash/.
It is possible to get the whole file without using tfpt or any other trickery by simply copying it accross into accessible area from webui:
cp /mnt/flash/Server.tar.xz /mnt/flash/web/browse/
From there you can simply type http://${camera_ip}/browse/Server.tar.xz and download the whole thing.
Examining the "server" binary I discovered major security flaw. Specifically in Server/LINUX/webs there are following strings:
name=HANKVISION
password=HANKVISIONI tested it against web ui, and to my horror these credentials allowed me to log in (with admin right nevertheless).
Here is the Server.tar.xz for curious types.
Other things.
The /etc/passwd contained the following:
root:$1$EnVGPLqH$OmqpejDjDsF8NQkcwH/og.:0:0::/root:/bin/sh
I am using JTR with Cuda (on GTX970) against it (at this stage alpha 4-8), but I doubt I will get anywhere. I need to find an exploit to change /etc/passwd without using serial.
The /etc/passwd- contained the following:
root:$1$y3A1TsGe$n7RvgOkNPb1PhGPGnh9v5.:0:0::/root:/bin/shThere are a lot of references to Justin and paths like /home/zhangxq/
Since you can get Server.tar.xz and there is wget, you can modify Server.tar.xz and replace modified version via wget, which opens to plenty of possibilities.